What Manufacturers Need to Know About the EU Cyber Resilience Act

21 Nov 2024
Complying with New Cybersecurity Requirements for Connected Products
The EU Cyber Resilience Act (CRA) was published in the Official Journal of the European Union (https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=OJ:L_202402847) on November 20, 2024, and it is set to reshape the cybersecurity landscape for digital products in Europe. Here’s a clear overview of what manufacturers need to understand about this pivotal regulation.
What Products fall under the Scope of the CRA?
The CRA applies to any product with digital elements connected directly or indirectly to a network. This broad scope includes household devices, consumer electronics, cloud-based software, and critical infrastructure components. It impacts companies that manufacture, import, or distribute such products within the EU, regardless of where the company is based.
Exceptions
While most connected products fall under the CRA, certain categories are excluded:
- Medical devices
- Automobiles
- Aviation and maritime equipment
These products are governed by their own specific regulations, ensuring overlapping compliance efforts aren’t necessary.
Essential Requirements
The CRA mandates that manufacturers adhere to certain key requirements:
- Secure by Design: Products must be designed, developed, and produced to ensure an appropriate level of cybersecurity based on the assessed risks.
Also, based on a cybersecurity risk assessment, products must address the following requirements:
- Availability Without Known Vulnerabilities: Products must be made available on the market without any known exploitable vulnerabilities.
- Secure by Default Configuration: Products should be offered in a secure default configuration, with an option to reset to the original state. Business users and manufacturers can agree on a different configuration for tailor-made products.
- Vulnerability Handling through Updates: Products must include mechanisms for handling vulnerabilities through security updates. These updates should ideally be automatic by default, with an option for users to opt out, and updates must be delivered promptly.
- Protection from Unauthorized Access: Products must protect against unauthorized access using mechanisms such as authentication, identity management, or other appropriate access control systems.
- Data Confidentiality: Products must ensure the confidentiality of both personal and non-personal data through encryption or similar state-of-the-art technical measures.
- Data Integrity: Products must protect data, commands, programs, and configuration from unauthorized modification, ensuring integrity and reporting any corruptions.
- Data Minimization: Products must only process data that is necessary, relevant, and limited to the intended purpose (data minimization).
- Availability of Essential Functions: Products must maintain the availability of essential functions, even after incidents, through resilience and mitigation measures, including protection against denial-of-service attacks.
- Minimize Impact on Other Services: Products must minimize their negative impact on the availability of services provided by other devices or networks.
- Limit Attack Surfaces: Products must be designed to limit attack surfaces, such as reducing unnecessary external interfaces.
- Incident Mitigation: Products must be designed to reduce the impact of incidents by employing exploitation mitigation mechanisms and techniques.
- Security Monitoring and Recording: Products must provide security-related information through monitoring and logging relevant activities, such as access to or modification of data, with the ability for users to opt out.
- Secure Data Removal: Products must provide a mechanism for users to easily and permanently remove all data and settings. Where possible, data should be transferred securely to other systems.
Additionally, manufacturers must meet the vulnerability handling requirements:
- Identification and Documentation: Manufacturers must identify and document vulnerabilities and components in their products, including by creating a Software Bill of Materials (SBOM). This SBOM should be in a commonly used, machine-readable format and cover at least the top-level dependencies of the products.
- Addressing Vulnerabilities: Vulnerabilities must be addressed and remediated without delay, including by providing security updates. Security updates, where technically feasible, should be delivered separately from functionality updates to ensure users receive necessary fixes promptly.
- Testing and Security Reviews: Products must undergo effective and regular security tests and reviews to ensure their safety from potential vulnerabilities.
- Public Disclosure of Fixed Vulnerabilities: Once a security update has been made available, manufacturers must publicly share information about the fixed vulnerabilities. If the risks associated with immediate disclosure outweigh the benefits, manufacturers may delay publication until users have had a chance to apply the patch.
- Policy on Coordinated Vulnerability Disclosure: Manufacturers must implement and enforce a coordinated vulnerability disclosure policy to ensure proper handling and reporting of vulnerabilities in their products.
- Information Sharing: Measures must be in place to facilitate the sharing of information about potential vulnerabilities, both for the product itself and for any third-party components. Manufacturers must also provide a contact address for vulnerability reports.
- Secure Distribution of Updates: Manufacturers must ensure that security updates are distributed securely. These updates should be provided to fix or mitigate vulnerabilities in a timely manner, and security updates should, where applicable, be installed automatically.
- Free and Timely Security Updates: Security updates should be disseminated without delay and provided free of charge. Updates should be accompanied by advisory messages that help users understand what actions they may need to take.
The Act also includes incident reporting obligations for manufacturers:
- Quick Notifications: Report any actively exploited vulnerabilities or severe incidents within 24 hours of awareness. Submit additional details within 72 hours, including general information and initial mitigation steps.
- Final Report: Provide a comprehensive report within 14 days for vulnerabilities and one month for severe incidents, detailing the issue, its severity, and applied fixes.
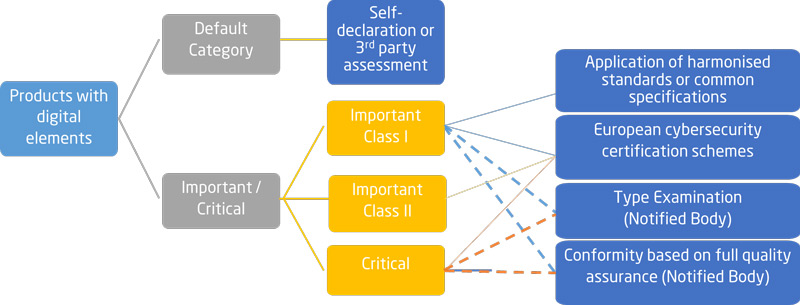
Product Classification
Product categories under the CRA include:
- Baseline Products: Everyday items like smart speakers and connected toys. Manufacturers can self-assess compliance.
- Important Products: Devices with higher risks, such as VPNs, biometric readers, and network management tools. These require stricter cybersecurity obligations and may need third-party assessments.
- Critical Products: High-risk items like smart meters and systems that could impact broad infrastructures. These face the most rigorous scrutiny.
The first step manufacturers should take is to determine if their products fall into the important or critical risk categories. The commission will adopt an implementing act to specify the technical descriptions of the categories of products by December 11, 2025.
Demonstrating Conformity
Under the Cyber Resilience Act, conformity for different classifications of products is demonstrated using the following procedures:
- Class I Products: Manufacturers can assess conformity internally if they apply harmonized standards or common specifications. Alternatively, they may opt for a third-party assessment. Manufacturers may also use a European Cybersecurity Certification Scheme.
- Class II Products: Manufacturers can involve a notified body to conduct a type examination or operate an approved quality system that is periodically audited by notified bodies. Manufacturers may also use a European Cybersecurity Certification Scheme.
- Critical Products: Conformity is demonstrated by using a European Cybersecurity Certification Scheme or by using procedures similar to Class II, if such a scheme is not available.
Timelines for Implementation
The CRA, published in the Official Journal on November 11, 2024, has the following transition timeline:
- December 11, 2025 – Commission to adopt implementing act specifying the technical description of the categories of products under classes I and II and critical products
- September 11, 2026 – Early incident reporting obligations apply
- December 11, 2027 – Full regulation applies
Penalties
Non-compliance with the CRA can result in severe penalties including fines up to EUR 15 million or 2.5% of global annual turnover. Manufacturers can also face product recalls and persistent violations may lead to product withdrawal from the EU market.
Final Thoughts
The CRA is part of the EU’s broader push for stronger cybersecurity standards across the region, aligning with other legislative efforts like the NIS2 Directive. Manufacturers need to prepare now by auditing their product lines, reviewing compliance documentation, and strengthening their cybersecurity practices to meet these upcoming requirements.
Intertek’s Cybersecurity team can support manufacturers today with services such as vulnerability assessments, workshops, and comprehensive gap analysis. These services help identify potential areas of non-compliance, enhance cybersecurity readiness, and facilitate a smooth transition to full CRA conformity.
